Defending Against Online Threats in Long-Term Care and Post-Acute Care
In today’s digital world, safeguarding your healthcare organization, especially long-term and post-acute care facilities, from cyber threats is crucial. Among the various risks, phishing attacks pose a constant and severe danger. In this blog post, we’ll explore phishing attacks, providing insights to help you recognize, defend against, and minimize their impact on your facility’s operations and patient data.
Understanding Phishing
Phishing is a cyber-attack method that tricks individuals into sharing sensitive information through deceptive tactics, such as usernames, passwords, or financial details. Attackers often impersonate trusted sources like colleagues, banks, or government agencies, aiming to compromise security by encouraging actions such as clicking on harmful links, downloading infected files, or divulging confidential information.
Spotting Phishing Emails
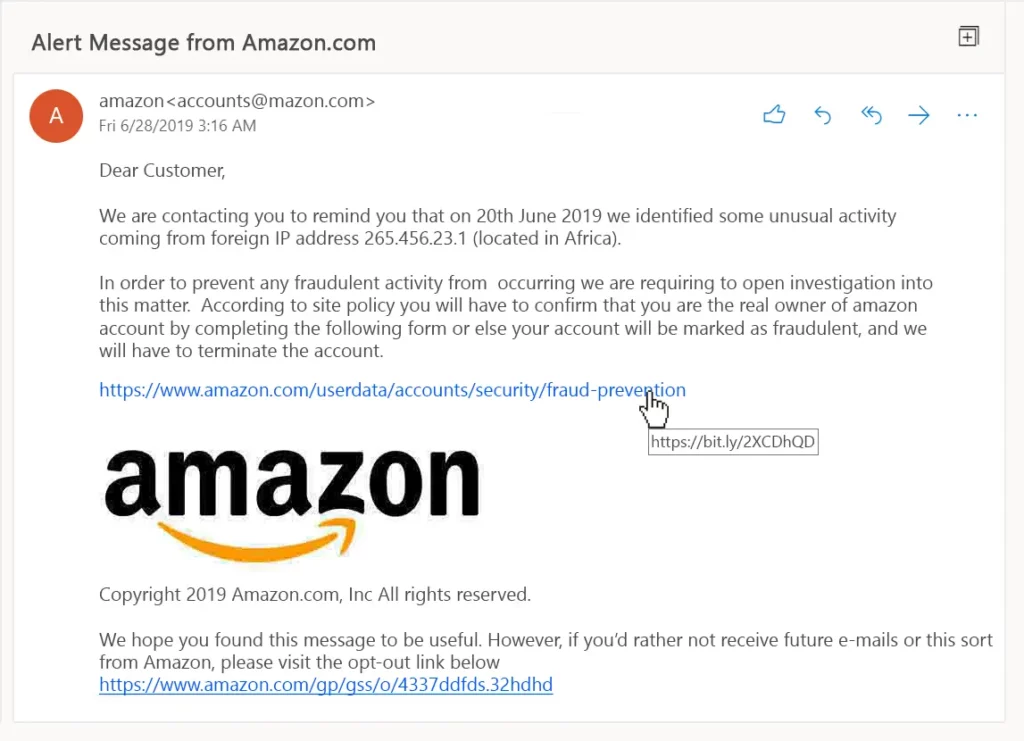
Recognizing phishing emails is the first step in defending against this cyber threat.
Here are some essential tips to help you and your team identify suspicious emails:
1. Check the Sender’s Address: Scrutinize the sender’s email address carefully, as phishers often use addresses that resemble legitimate ones but contain minor misspellings or alterations.
2. Watch for Generic Greetings: Avoid emails using generic greetings like “Dear User” instead of addressing you by name. Legitimate organizations typically personalize their communications.
3. Verify Links and Hover Over Them: Hover your mouse pointer over any links in the email to see the actual URL. Ensure it matches the official website of the supposed sender.
4. Beware of Urgency and Threats: Phishing emails often create a sense of urgency or threat to pressure recipients into quick actions. Stay wary of messages that demand immediate responses.
5. Check for Spelling and Grammar Mistakes: Phishers might overlook details. Poorly written emails with spelling and grammar mistakes can signal a potential threat.
Educating Employees is Crucial
Education is vital in defending against phishing attacks. Investing in ongoing training for your team is essential to ensure they are well informed about the risks and prevention measures. Consider the following steps:
Conduct Phishing Awareness Workshops: Arrange workshops or training sessions that simulate phishing attacks to help employees recognize and respond to phishing attempts.
Teach Safe Email Practices: Train employees to avoid clicking suspicious links or downloading attachments from unknown sources. Please encourage them to verify the legitimacy of email requests.
Establish Reporting Procedures: Make sure your team knows how to report suspected phishing attempts promptly. Create a clear and user-friendly reporting protocol.
Enhancing Security with Multi-Factor Authentication (MFA)
Implementing multi-factor authentication (MFA) provides an added layer of protection for your email accounts and systems. MFA requires users to provide two or more forms of identification before granting access. Even if a cybercriminal obtains login credentials, they won’t be able to access accounts without the additional authentication step.
Reporting Incidents
If a phishing attempt succeeds, having an incident response plan is crucial. Establish clear protocols for reporting security incidents, including phishing attacks. A swift response can help mitigate potential damage and prevent further compromise of sensitive data.
In conclusion, phishing attacks pose a significant threat to healthcare facilities. However, with proper education, vigilance, and security measures, you can significantly reduce the risk of falling victim to these scams. By understanding phishing, recognizing phishing emails, providing employee training, implementing MFA, and establishing incident reporting procedures, your long-term care or post-acute care facility can bolster its cybersecurity defenses, protecting patient data and organizational integrity. Stay safe, stay informed, and remain vigilant in the ever-evolving landscape of cyber threats.
Phish Tales
Take an adventure through our simple, and fun, online phishing education course.